Uncover Weaknesses Before Attackers Do
At The Hidden Finds, our Penetration Testing-as-a-Service (PTaaS) is designed to expose and eliminate security flaws in your infrastructure—before threat actors can exploit them. By mimicking the behavior of real-world attackers, our ethical hackers simulate advanced intrusion attempts across your networks, applications, and cloud environments. The result? Actionable insights that significantly enhance your organization’s security posture.
“Think like a hacker—defend like a pro.”
Penetration Testing, often called Pen Testing, is the controlled simulation of a cyberattack against your systems, designed to uncover vulnerabilities that traditional defenses might miss. With PTaaS from The Hidden Finds, we take it a step further by offering continuous, expert-led testing that replicates real-world threat scenarios using the same tools, tactics, and procedures employed by malicious actors.
This service provides not only a thorough vulnerability analysis, but also a detailed report with prioritized recommendations—allowing you to proactively fix gaps and reduce risk long before a real incident can occur.
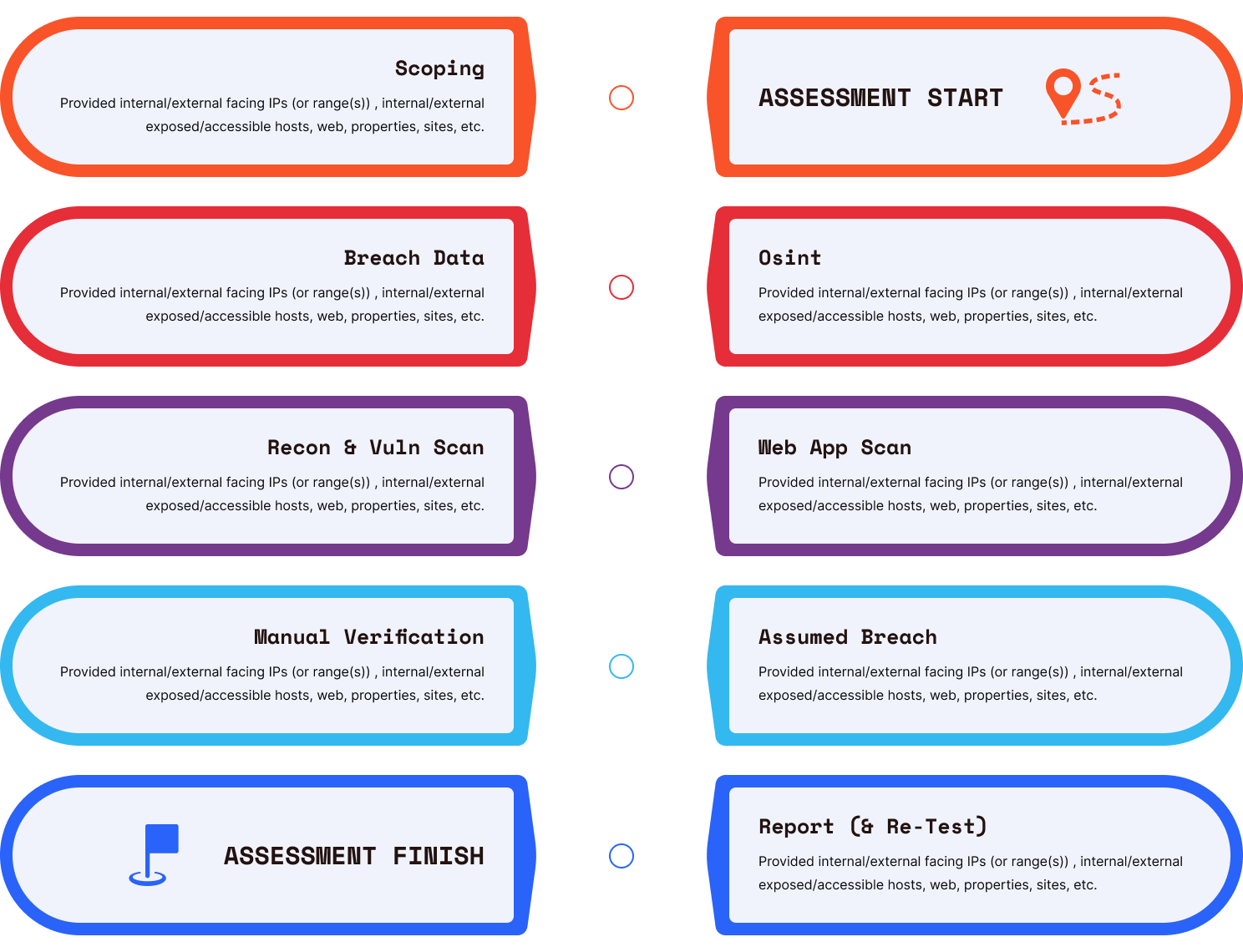

Simulates real-world attacks to identify vulnerabilities in websites, portals, and APIs.

Evaluates internal network security by mimicking insider threats or compromised employee access.

Assesses mobile apps for security flaws in code, APIs, data storage, and user authentication.
The Hidden Finds conducts “ethical hacking” against commonly used security methods, such as MAC authentication, WEP, WPA, and WPA-2, to penetrate wireless access points (APs). The objective of this assessment is to gain unauthorized access to the network.
The Hidden Finds conducts “ethical hacking” against commonly used security methods, such as MAC authentication, WEP, WPA, and WPA-2, to penetrate wireless access points (APs). The objective of this assessment is to gain unauthorized access to the network.
The Hidden Finds conducts “ethical hacking” against commonly used security methods, such as MAC authentication, WEP, WPA, and WPA-2, to penetrate wireless access points (APs). The objective of this assessment is to gain unauthorized access to the network.
The Hidden Finds conducts “ethical hacking” against commonly used security methods, such as MAC authentication, WEP, WPA, and WPA-2, to penetrate wireless access points (APs). The objective of this assessment is to gain unauthorized access to the network.
Your biggest vulnerability may be human.
During our Social Engineering testing, we simulate targeted phishing, vishing (voice phishing), and malicious USB drop campaigns to evaluate employee awareness and incident response. These include:
With The Hidden Finds, you’re not just checking boxes—you’re building resilience. Our Penetration Testing-as-a-Service helps you stay ahead of attackers, meet compliance requirements, and build customer trust.
Get in touch today to schedule a consultation or demo, and let our experts help you take proactive control over your security.

© 2025 The Hidden Finds | All Rights Reserved | Powered by farazdev.io